When you set up a new account, you are often asked to create a password and choose a security question and answer (e.g., What is your mother’s maiden name?). Answering security questions based on personal information when you log in to an app or system is called knowledge-based authentication (KBA). While KBA is still widely used, people freely share the same information on social media sites, reducing its security value.
This article was originally published by PingIdentity.
Passwords are also shared, stolen, or figured out with password cracking tools. A 2020 study by the Digital Shadows Photon Research Team found that 15 billion stolen credentials, including username-password combinations, were available on the dark web. Because a user’s password and KBA can both be obtained by bad actors, enterprises relying on those weak authentication methods need to reinforce them with more secure methods. It’s like reinforcing a flimsy screen door with a solid door and deadbolt to keep your home safe.
Read on to learn more about KBA, its uses, limitations and reinforcements.
What is Knowledge-Based Authentication (KBA)?
Enterprises use knowledge-based authentication to verify a user’s identity based on something the user knows. The information can come directly from the user, like a phone number, current address or answers to security questions they provide during registration, or the enterprise can obtain the information from data brokers and other sources.
Static Knowledge-Based Authentication (SKBA)
Most people are familiar with static KBA, which is sometimes referred to as a shared secret. This goes beyond basic information, such as an address or phone number. When a user creates an account, they are required to provide an answer to one or more security questions. They can provide accurate information or make up answers, as long as they remember the answers when prompted at a later date. Enterprises need to be careful when selecting the type and number of questions they require, because people find intrusive or excessive questions annoying.
Dynamic Knowledge-Based Authentication (DKBA)
While dynamic KBA provides a higher level of security, it is used less frequently. Dynamic KBA relies on information collected from different data sources to generate real-time questions. For example, a user may be asked, “Which of the following companies did you not work for?” and be presented with a list of three former employers and one incorrect answer. Your users may be unnerved when they see the depth and breadth of information you are able to obtain about them. DKBA is also a more expensive option for enterprises than SKBA.
How Secure is Knowledge-Based Authentication (KBA)?
The personal information used for KBA can often be discovered or stolen through research, phishing and social engineering, and used to commit online fraud. In addition to bad actors finding personal information posted on people’s social media accounts or other online sites, they can also use social engineering to create quizzes and post questions to obtain specific information. According to a Cyber Florida report, “Nearly 40 percent of social media users surveyed had completed a quiz or played a game that appeared in their feed in an average week.”
Some people also respond to seemingly random questions on social media. For example, someone on Facebook may ask: “I really miss my cat, Sir Fluffball. What was the name of your favorite pet?” A random Twitter user may post: “What is your hometown known for?” Without thinking about the consequences, people post answers for all to see. Fraudsters already in possession of compromised credentials (username-password combinations) can look through the social media profiles of people answering questions or participating in quizzes to find matches in order to commit account takeover fraud. Social media users that include their full name along with location, phone number, high school, favorite band, family members and other details of their life make it easier for cybercriminals to hack their accounts.
Is Knowledge-Based Authentication (KBA) User-friendly?
Customers want a frictionless experience, which is why having to select from a list of security questions and provide answers is so frustrating. Questions about family members or pets can also be hurtful if the person or pet is sick or has passed away. Users may abandon the process before they complete the registration process.
For users that do complete the process, it may be weeks or months before they are asked for the answer to a security question. Anyone who has forgotten a password or answer to a security question knows the frustration of trying to reach an IT help desk for assistance if a self-service option isn’t available. Irritated customers may give up and use a competitor instead.
Reinforcing Knowledge-Based Authentication (KBA) with Multi-factor Authentication (MFA)
Multi-factor authentication (MFA) and two-factor authentication (2FA) require users to provide proof of their identity from two or more authentication factors. Authentication factors include:
- Knowledge – Something you know. This includes KBA, passwords, PINs and other types of information that users share with enterprises.
- Possession – Something you have. This can be a token generated by a transaction or an application, such as a one-time password sent to your mobile device. It could also come from a hard token, like a USB-based device or separate code generator.
- Biometric – Something you are. This is an inherited trait and confirmed with a scan, such as a fingerprint scan, facial recognition or a retinal scan. Biometrics require some sort of scanner, such as a smartphone.
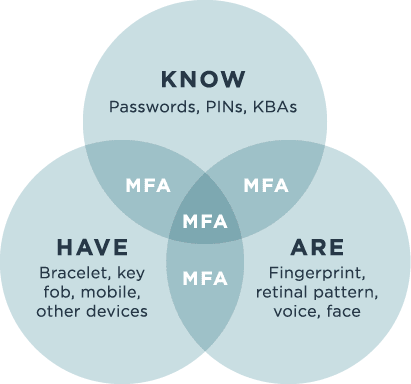
Using two authentication methods from the same factor, such as a password and answer to a security question from the Knowledge category, is less secure than multi-factor authentication and two-factor authentication. Bad actors who obtain compromised passwords and answers to security questions rarely have access to Possession or Biometric factors too. In fact, according to Microsoft, MFA can prevent 99.9 percent of attacks on your accounts.
Watch this short video to see how multi-factor authentication (MFA) takes knowledge-based authentication (KBA) to the next level to increase security, improve the user experience and prevent data breaches.


