This blog post covers a sophisticated QR code based phishing which uses a unique approach of multilayered malicious QR code attack to deceive email filtering systems.
This post was originally published in Proofpoint.
Use Case: Multilayered Malicious QR Code Attacks

Problem Statement
The convenience of QR codes sometimes becomes the target of a deceptive phishing attack, with cybercriminals using multilayered tactics to disguise the landing page URL as a legitimate website.
Realization Approach
An intelligent email threat protection system can identify a malicious QR code even if it is hidden within an attached PDF and protected by a seemingly benign looking CAPTCHA check.

Solution Space
With multilayered email threat protection, it is possible to further minimize the impact of phishing attacks compared to traditional approaches that rely solely on URL reputation and spam content checks on email message text.
The Scenario
Typically, in a QR code attack a malicious QR code is directly embedded in an email. But recently, attackers have come up with a new and sophisticated variation. In these multilayered attacks, the malicious QR code is hidden in what seems like a harmless PDF attachment. To slow down automated detection and confuse traditional email security tools, attackers use anti-evasion tactics like adding a Cloudflare CAPTCHA. This means that tools using traditional URL reputation detection face an uphill battle in trying to identify them.
Proofpoint recently found one of these threats as it conducted a threat assessment at a U.S.-based automotive company with 11,000 employees. The company’s incumbent security tools—an API-based email security tool and its native security—both boasted QR scanning capabilities. Yet both classified the email as clean and delivered it to the end user.
The threat: How did the attack happen?
Here’s a closer look at how the attack unfolded.
1. A deceptive lure. The email was designed to appear legitimate, and it played on the urgency of tax season. This prompted the recipient to open an attached PDF.
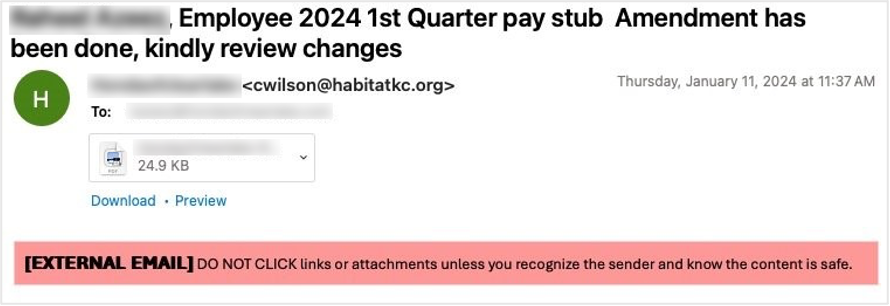
The initial email to the end user.
2. Malicious QR code embedded in the PDF. Unlike previous QR code attacks, the malicious URL in this attack was not directly visible in the email. Instead, it was hidden in the attached PDF. Given the ubiquity of QR codes, this might not have seemed suspicious to the recipient.

The attached PDF with the embedded QR code (obscured).
3. Cloudflare CAPTCHA hurdle. The attacker added another layer of deception. They used a Cloudflare CAPTCHA on the landing page from the QR code URL to further hide the underlying threat. This step aimed to bypass security detection tools that rely solely on analyzing a URL’s reputation.
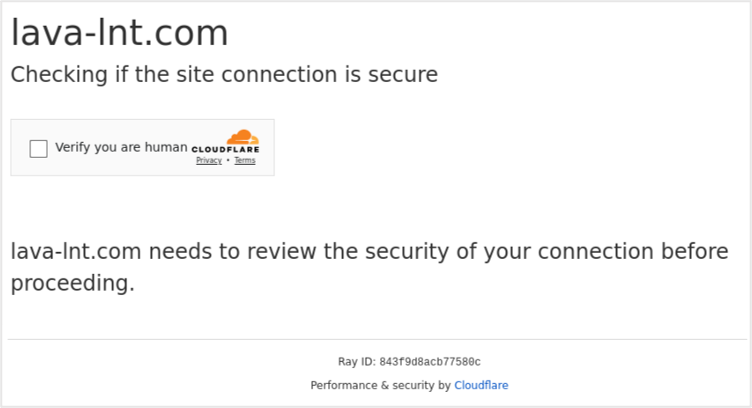
Cloudflare CAPTCHA on the QR code URL landing page.
4. Credential phishing endgame. Once the CAPTCHA was solved, the malicious QR code led to a phishing landing page set up to steal user credentials. The theft of user credentials can give a malicious actor access to a user’s account to spread attacks internally for lateral movement. Or they might use them externally to deceive partners or suppliers as with supplier email compromise attacks.
Detection: How Did Proofpoint Prevent This Attack?
The use of optical character recognition (OCR) or other QR code scanning techniques plays a vital role in defending against QR code threats. But QR code scanning is only the mechanism used to extract the hidden URL. It does not act as a detection mechanism to decipher between legitimate or malicious QR codes.
Many tools, including the incumbent email security tools used by the automotive company, claim to parse QR codes and extract the URL for analysis. However, they lack the ability to scan URLs within an embedded image in an attachment. Few tools have engineered the ability to use in-depth URL analysis on a scale like Proofpoint.
Proofpoint uses QR code scanning, but we combine it with a multilayered detection stack that uses advanced artificial intelligence (AI) and machine learning (ML) techniques to understand the context of email correspondence. We tightly intertwine our deep threat analysis techniques and sandboxing to ensure the proper detection of advanced QR code threats.
Here’s what we used to detect and stop this threat:
- QR code scanning. Proofpoint uses QR code scanning to convert images into a machine-readable format. This allowed us to extract the hidden URL in this attack for further analysis. Our QR code scanning supports various scenarios including PDF, email body, images, Microsoft Word files and many others. Support for QR code scanning plays a foundational role in defending against these types of threats.
- Behavioral indicators. Proofpoint analyzed user behavior, email context and the thematic nature of the email. This, in turn, allowed us to detect patterns that indicated a high likelihood of the email being malicious.
- URL sandboxing. With the URL extracted within a sandbox, Proofpoint can analyze visual elements, redirect patterns, endpoint processes, network activity, DNS calls, and CPU and memory processes. We can detect anti-evasion tactics like CAPTCHAs as well. Proofpoint detects advanced URL threats that other tools struggle to detect because we analyze the URL and its behavior. Even if the URL is found to be clean despite showing behavioral indicators associated with malicious activity, we continue to monitor and scan the URL for later compromise or weaponization.
Remediation: What Are The Lessons Learned?
This attack highlights the evolving nature of phishing tactics that use QR codes. And it underscores the importance of using a multilayered email security approach. Here are some key takeaways:
- Be cautious of all requests to scan QR codes. Do not automatically trust PDFs, images or other requests to scan QR codes, especially those that arrive in unsolicited emails.
- Stay vigilant during tax season. Phishing attempts create a sense of urgency and often exploit time-sensitive events.
- Look beyond URL reputation. Advanced email threats can bypass traditional reputation-based filters and API-based email security tools.
- Invest in comprehensive security. Choose tools that combine threat intelligence, behavioral analysis and advanced technologies like OCR and URL sandboxing.
- Security awareness training. Empower your employees to identify suspicious QR codes, question unexpected requests and proactively report them.
Proofpoint Delivers Human-Centric Security
The multilayered QR code attack in this example aimed to bypass traditional defenses, but Proofpoint and our Human-Centric Security stopped it in its tracks. Advanced threat intelligence and detection capabilities—like QR code scanning, OCR, behavioral AI, and URL sandboxing—allowed us to identify this deception quickly and protect users from harm.
Don’t wait for your company to become the next target. Empower your people and secure your business with Proofpoint.
To learn more about how Proofpoint can help your business defend against threats like QR code phishing attacks, download our e-book, The Definitive Email Cybersecurity Strategy Guide.


